Automatic provisioning, configuration files, and clients
Zitat von mpachmann am 13. Juni 2025, 9:15 Uhrhttps://docs.sophos.com/nsg/sophos-firewall/21.5/help/en-us/webhelp/onlinehelp/AdministratorHelp/RemoteAccessVPN/IPsecSSL/SophosConnect/RAVPNSConClientsConfigurations/index.html
You can use the provisioning file to automatically import remote access IPsec VPN and remote access SSL VPN configurations to the Sophos Connect client.
Alternatively, users can download the individual configuration files.
Requirements
When the provisioning file is used, the Sophos Connect client imports the configuration through the VPN portal. For remote users connecting from the WAN zone, you must allow WAN access for the VPN portal in Administration > Device access, under Local service ACL.
Microsoft Entra ID SSO requirements
To use Microsoft Entra ID single sign-on (SSO) when deploying a remote access IPsec VPN or remote access SSL VPN, you must meet the following requirements.
Provisioning workflow
When deploying a remote access IPsec VPN or remote access SSL VPN using a provisioning file, you must meet the following requirements:
- The VPN portal, IPsec VPN, and SSL VPN authentication methods must use the same Microsoft Entra ID server in Authentication > Services.
- The
gatewaysetting in the provisioning file must match the Redirect URI of the Microsoft Entra ID server configured in the firewall.Non-provisioning workflow
When deploying a remote access IPsec VPN or remote access SSL VPN using a configuration file, you must meet the following requirements:
- You must first configure the Microsoft Entra ID server as an authentication method in Authentication > Services before downloading the VPN configuration file. Otherwise, the SSO authentication won't work.
- For remote access SSL VPN, the VPN portal and SSL VPN authentication methods must use the same Microsoft Entra ID server in Authentication > Services.
- For remote access IPsec VPN, you can use the same or a different Microsoft Entra ID server as the authentication method in Authentication > Services.
Provisioning file
When users double-click the provisioning (
.pro) file, it's imported into the Sophos Connect client. Based on the.profile settings, the client connects to the VPN portal and automatically imports the remote access SSL VPN (.ovpn) file corresponding to the user and the remote access IPsec (.scx) file into the Sophos Connect client.You can configure the provisioning file in a text editor and save it with a
.proextension. To know the operating systems on which you can use the Sophos Connect client and provisioning file, see Sophos Connect client.Installing the provisioning file
You can share the
.profile with users. See Provisioning file templates.Alternatively, you can directly install it on users' endpoints using Active Directory Group Policy Object (GPO) in the following folder:
C:\Program Files (x86)\Sophos\Connect\import. The Sophos Connect client will automatically import the.profile from the folder.See Import VPN provisioning file through GPO.
Fetching configurations
After importing the provisioning file, the client automatically fetches the available VPN (
.scxand.ovpn) configurations.See the following behavior for configuration changes you make later:
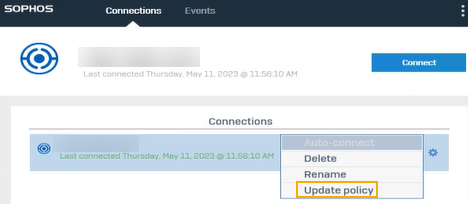
- If you change the port or protocol on SSL VPN global settings, users must click the gear button for the configuration in the Sophos Connect client and click Update policy.
- The client automatically fetches any other configuration changes you make.
- Some configuration changes in SSL VPN global settings, such as port, gateway, SSL server certificate, and protocol, require users to sign in to the Sophos Connect client again.
Configuration files
These files are created when you configure the IPsec remote access connection and the SSL VPN remote access settings and policies.
IPsec: Go to Remote access VPN > IPsec and click Export connection to download the files. You must share one of the following configuration files manually with users:
.scxfile: You can only use this file with the Sophos Connect client. It contains advanced settings in addition to the other settings. You configure all the settings on the web admin console. We recommend that you use this file.If you update any of the advanced settings, send the updated
.scxconfiguration file to users for import into the Sophos Connect client..tgbfile: You can use this file with third-party clients. It doesn't contain the advanced settings you configure.- iOS users can download the configuration file directly from the VPN portal (VPN > VPN configuration under IPsec VPN profile).
SSL VPN: It uses the
.ovpnconfiguration file. On the VPN portal, users can download the file from VPN > VPN configuration under SSL VPN configuration. They can select the configuration file that's compatible with the client they use.Clients and configurations
The clients you can use depends on the connection type and the endpoint device. See the client, provisioning file, and configuration file details in the following table:
Type of remote access VPN Client Provisioning and configuration files IPsec Sophos Connect client. For mobile platforms, you can use the OpenVPN Connect client.
Users download the client from the VPN portal.
You can share one of the following files with users:
.pro(recommended): Share the provisioning file with users. It automatically imports the configuration file to the client.You can use the provisioning file for remote access IPsec VPNs. Additionally, users must install the Sophos Connect client 2.1 or later.
.scx: Use this configuration file rather than the.tgbfile for advanced security settings. You must share it with users.
.tgbiOS users must download the configuration file from the VPN portal.
IPsec (legacy) Third-party VPN clients .tgb: Share the file with users.SSL VPN Sophos Connect client You can use one of the following methods:
.pro(recommended): Share the provisioning file with users. They can click the file to import the.ovpnfile to the Sophos Connect client.
.ovpn: Users directly download the file from the VPN portal for the Sophos Connect and OpenVPN Connect clients.SSL VPN For macOS, you can use third-party VPN clients. For mobile platforms, you can use the OpenVPN Connect client.
.ovpn: Users download the file from the VPN portal.Template:
https://docs.sophos.com/nsg/sophos-firewall/21.5/help/en-us/webhelp/onlinehelp/AdministratorHelp/RemoteAccessVPN/IPsecSSL/SophosConnect/RAVPNSConProvisioningFile/index.html
The Sophos Connect provisioning file allows you to provision remote access IPsec VPN and remote access SSL VPN connections with Sophos Firewall. If you've configured the IPsec remote access settings, the provisioning file automatically imports the
.scxconfiguration file into the Sophos Connect client for all users. It only imports the.ovpnconfiguration file for users you've assigned to an SSL VPN remote access policy.It also automatically imports any configuration changes you make later. Users don't need to download the configuration file from the VPN portal.
Note
You can use the provisioning file for remote access IPsec VPNs. Users must install the Sophos Connect client 2.1 or later.
Benefits
Using the provisioning file offers the following benefits:
- Automatically imports the IPsec remote access (
.scx) and SSL VPN remote access (.ovpn) configuration files into the Sophos Connect client on users' endpoints. You don't need to share the.scxfile with users.Users won't need to sign in to the VPN portal and download the
.ovpnfile.- Automatically imports any configuration changes you make later.
- Allows you to specify more than one gateway and their priority.
Configure the provisioning file
You can configure the provisioning file and share it with users. Alternatively, you can deploy it on users' endpoints through Active Directory Group Policy Management (GPO).
Provisioning file settings
Setting Description gatewayThe FQDN or IPv4 address of the firewall that provisions the connection. When using Microsoft Entra ID single sign-on (SSO), this setting must match the Redirect URI of the Microsoft Entra ID server configured in the firewall. See Requirements.
gateway_orderSpecifies how Sophos Firewall balances traffic when multiple gateways are configured. The allowed values are as follows:
distributed: Selects a gateway at random when a connection is attempted.
latency: Selects a gateway by how quickly it responds to a TCP connect request.
in_order: Tries the first gateway in the list first, if that fails, the next gateway is tried.vpn_portal_portYou can use the vpn_portal_portsyntax to enter the VPN portal port. It's the port on which the provisioning connection is made.If you change the port in the firewall, you must change it in the provisioning file.
Default port: 443.
You can continue to use the
user_portal_portsyntax, but you must enter the VPN portal's port.auto_connect_hostThe target host used to determine if the Sophos Connect client is already on the internal network. If a value is supplied, the Sophos Connect client checks if the host is reachable each time a network interface IP address is obtained or modified. If the host isn't reachable, then the connection is automatically enabled, and if the credentials are saved, then the VPN tunnel is established. Default: empty string
""(auto-connect disabled).To turn on auto-connect, set it to an IP address or hostname that exists on the remote LAN network.
If the last login method is SSO and the
auto_connect_hostisn't reachable, the Sophos Connect client will automatically authenticate the user using SSO and establish the VPN tunnel.can_save_credentialsAllows users to save their username and password for the connection. If you enter true, a checkbox appears on the user authentication page. The checkbox is checked by default but the user can decide not to save credentials.Allowed values:
trueorfalse.Default value: true.
This setting isn't applicable for the SSO login method.
check_remote_availabilityPerforms a remote availability check at connection startup to eliminate unresponsive clients. Allowed values:
trueorfalse.Default value: true.
run_logon_scriptRuns the logon script provided by the domain controller after the VPN tunnel is established. Allowed values:
trueorfalse.Default value: false.
Templates
You can use the following provisioning file templates to create provisioning files specific to your organization. You can change the settings.
Copy and paste the scripts in a text editor, such as Notepad, edit the settings to meet your requirements, and save the file with a
.proextension.Requirement
You must specify the gateway address. The other fields are optional.
Note
If you change the VPN portal port in the firewall, you must change it in the provisioning file.
Single connection
Multiple connections
Multiple gateways
Provisioning file: 2FA settings
Setting Description otpSpecifies if a one-time password (OTP) is required for authentication when connecting. This shows a third input box to enter the OTP code in the Sophos Connect client. Allowed values:
trueorfalse.Default value: false.
2faSpecifies the method of two-factor authentication (2FA) to use. Allowed values:
1or2.Default value: 1.
The allowed values are as follows:
1Uses the Sophos Firewall configuration for 2FA. Users must enter the OTP token or the verification code in the third input field. The OTP token or verification code is appended to the password (example:passwordotp) and sent to the authentication server. Users can generate the token using authenticator apps, such as Google Authenticator.
2Uses an external 2FA server, such as Duo. Users must enter the verification code generated by the authenticator app in the third input field. The password and verification code are comma-separated and sent to the authentication server. See Third-party authenticator support.If you've configured more than one Duo method, users must enter the following in the third input box:
- Duo Push:
push- Duo phone:
phone- Duo SMS:
sms(The sign-in screen appears again. Users must enter the username, password, and verification code.)- Duo token: The passcode.
Note
If users need to enter an OTP token or code, the Sophos Connect client shows the sign-in screen twice when they sign for the first time. The first sign-in downloads the configuration file and the second establishes the connection.
Templates
Sophos Firewall 2FA with OTP
Duo 2FA
Deploy provisioning File per gpo:https://docs.sophos.com/nsg/sophos-firewall/21.5/help/en-us/webhelp/onlinehelp/AdministratorHelp/RemoteAccessVPN/IPsecSSL/SophosConnect/RAVPNSConProvisioningFileGPOScript/index.html#import-provisioning-file-to-sophos-connect-clientYou can automatically download and import the remote access VPN provisioning file (
.pro) to the Sophos Connect clients on users' endpoints using a script through Active Directory Group Policy Object (GPO).Import provisioning file to Sophos Connect client
To download and import the provisioning file, do as follows:
- Open a blank file in a text editor, such as Notepad, and paste the following script:
@echo off REM Use the automatic import feature of the Sophos Connect client to download and import the .pro file REM Wait for scvpn service to be available :WAIT2 timeout /t 5 > NUL for /f "tokens=4" %%s in ('sc query scvpn ^| find "STATE"') do if NOT "%%s"=="RUNNING" goto WAIT2 echo Service is now running! REM scvpn service is available. Download the .pro file from a centrally-hosted location. Make sure you enter your URL and the filename you want. powershell -Command "Invoke-WebRequest <full_web_url_where_pro_file_is_hosted> -OutFile download_import_scc.pro" REM Copy the downloaded .pro file to the SCC import folder for the automatic import feature to act copy download_import_scc.pro "C:\Program Files (x86)\Sophos\Connect\import\"Note
The script waits for the scvpn service to run after the endpoint starts. So, don't stop the Sophos Connect service in your startup apps.
- Save the file with a
.batextension.- To add the path where you've saved the script, do as follows:
- On the Windows Server, open Group Policy Management Console (GPMC) and click Group Policy Management.
- Click the group policy that applies to users' endpoints, click Computer Configuration, and click Policies.
- Under Windows Settings, click Scripts, and double-click Startup.
- Follow the instructions to add the
.batfile. See Working with startup scripts using the Local Group Policy Editor.- To apply the script, run the following command:
gpupdate /forceWhen users start their endpoints, the
scvpnservice starts, and the script downloads the.profile from the server to the Sophos Connect import folder.The Sophos Connect client automatically imports the
.profile from this folder and deletes the file from the folder. It then connects to the VPN portal through the gateway configured in the.profile and pulls the remote access IPsec VPN and remote access SSL VPN configurations.
You can use the provisioning file to automatically import remote access IPsec VPN and remote access SSL VPN configurations to the Sophos Connect client.
Alternatively, users can download the individual configuration files.
Requirements
When the provisioning file is used, the Sophos Connect client imports the configuration through the VPN portal. For remote users connecting from the WAN zone, you must allow WAN access for the VPN portal in Administration > Device access, under Local service ACL.
Microsoft Entra ID SSO requirements
To use Microsoft Entra ID single sign-on (SSO) when deploying a remote access IPsec VPN or remote access SSL VPN, you must meet the following requirements.
Provisioning workflow
When deploying a remote access IPsec VPN or remote access SSL VPN using a provisioning file, you must meet the following requirements:
- The VPN portal, IPsec VPN, and SSL VPN authentication methods must use the same Microsoft Entra ID server in Authentication > Services.
- The
gatewaysetting in the provisioning file must match the Redirect URI of the Microsoft Entra ID server configured in the firewall.
Non-provisioning workflow
When deploying a remote access IPsec VPN or remote access SSL VPN using a configuration file, you must meet the following requirements:
- You must first configure the Microsoft Entra ID server as an authentication method in Authentication > Services before downloading the VPN configuration file. Otherwise, the SSO authentication won't work.
- For remote access SSL VPN, the VPN portal and SSL VPN authentication methods must use the same Microsoft Entra ID server in Authentication > Services.
- For remote access IPsec VPN, you can use the same or a different Microsoft Entra ID server as the authentication method in Authentication > Services.
Provisioning file
When users double-click the provisioning (.pro) file, it's imported into the Sophos Connect client. Based on the .pro file settings, the client connects to the VPN portal and automatically imports the remote access SSL VPN (.ovpn) file corresponding to the user and the remote access IPsec (.scx) file into the Sophos Connect client.
You can configure the provisioning file in a text editor and save it with a .pro extension. To know the operating systems on which you can use the Sophos Connect client and provisioning file, see Sophos Connect client.
Installing the provisioning file
You can share the .pro file with users. See Provisioning file templates.
Alternatively, you can directly install it on users' endpoints using Active Directory Group Policy Object (GPO) in the following folder: C:\Program Files (x86)\Sophos\Connect\import. The Sophos Connect client will automatically import the .pro file from the folder.
See Import VPN provisioning file through GPO.
Fetching configurations
After importing the provisioning file, the client automatically fetches the available VPN (.scx and .ovpn) configurations.
See the following behavior for configuration changes you make later:
- If you change the port or protocol on SSL VPN global settings, users must click the gear button for the configuration in the Sophos Connect client and click Update policy.
- The client automatically fetches any other configuration changes you make.
- Some configuration changes in SSL VPN global settings, such as port, gateway, SSL server certificate, and protocol, require users to sign in to the Sophos Connect client again.
Configuration files
These files are created when you configure the IPsec remote access connection and the SSL VPN remote access settings and policies.
IPsec: Go to Remote access VPN > IPsec and click Export connection to download the files. You must share one of the following configuration files manually with users:
.scxfile: You can only use this file with the Sophos Connect client. It contains advanced settings in addition to the other settings. You configure all the settings on the web admin console. We recommend that you use this file.If you update any of the advanced settings, send the updated
.scxconfiguration file to users for import into the Sophos Connect client..tgbfile: You can use this file with third-party clients. It doesn't contain the advanced settings you configure.- iOS users can download the configuration file directly from the VPN portal (VPN > VPN configuration under IPsec VPN profile).
SSL VPN: It uses the .ovpn configuration file. On the VPN portal, users can download the file from VPN > VPN configuration under SSL VPN configuration. They can select the configuration file that's compatible with the client they use.
Clients and configurations
The clients you can use depends on the connection type and the endpoint device. See the client, provisioning file, and configuration file details in the following table:
| Type of remote access VPN | Client | Provisioning and configuration files |
|---|---|---|
| IPsec | Sophos Connect client.
For mobile platforms, you can use the OpenVPN Connect client. Users download the client from the VPN portal. |
You can share one of the following files with users:
You can use the provisioning file for remote access IPsec VPNs. Additionally, users must install the Sophos Connect client 2.1 or later.
iOS users must download the configuration file from the VPN portal. |
| IPsec (legacy) | Third-party VPN clients | .tgb: Share the file with users. |
| SSL VPN | Sophos Connect client | You can use one of the following methods:
|
| SSL VPN | For macOS, you can use third-party VPN clients.
For mobile platforms, you can use the OpenVPN Connect client. |
.ovpn: Users download the file from the VPN portal. |
Template:
If you've configured the IPsec remote access settings, the provisioning file automatically imports the .scx configuration file into the Sophos Connect client for all users. It only imports the .ovpn configuration file for users you've assigned to an SSL VPN remote access policy.
It also automatically imports any configuration changes you make later. Users don't need to download the configuration file from the VPN portal.
Note
You can use the provisioning file for remote access IPsec VPNs. Users must install the Sophos Connect client 2.1 or later.
Benefits
Using the provisioning file offers the following benefits:
- Automatically imports the IPsec remote access (
.scx) and SSL VPN remote access (.ovpn) configuration files into the Sophos Connect client on users' endpoints. You don't need to share the.scxfile with users.Users won't need to sign in to the VPN portal and download the
.ovpnfile. - Automatically imports any configuration changes you make later.
- Allows you to specify more than one gateway and their priority.
Configure the provisioning file
You can configure the provisioning file and share it with users. Alternatively, you can deploy it on users' endpoints through Active Directory Group Policy Management (GPO).
Provisioning file settings
| Setting | Description |
|---|---|
gateway |
The FQDN or IPv4 address of the firewall that provisions the connection.
When using Microsoft Entra ID single sign-on (SSO), this setting must match the Redirect URI of the Microsoft Entra ID server configured in the firewall. See Requirements. |
gateway_order |
Specifies how Sophos Firewall balances traffic when multiple gateways are configured.
The allowed values are as follows:
|
vpn_portal_port |
You can use the vpn_portal_port syntax to enter the VPN portal port. It's the port on which the provisioning connection is made.
If you change the port in the firewall, you must change it in the provisioning file. Default port: 443. You can continue to use the |
auto_connect_host |
The target host used to determine if the Sophos Connect client is already on the internal network. If a value is supplied, the Sophos Connect client checks if the host is reachable each time a network interface IP address is obtained or modified. If the host isn't reachable, then the connection is automatically enabled, and if the credentials are saved, then the VPN tunnel is established.
Default: empty string To turn on auto-connect, set it to an IP address or hostname that exists on the remote LAN network. If the last login method is SSO and the |
can_save_credentials |
Allows users to save their username and password for the connection. If you enter true, a checkbox appears on the user authentication page. The checkbox is checked by default but the user can decide not to save credentials.
Allowed values: Default value: true. This setting isn't applicable for the SSO login method. |
check_remote_availability |
Performs a remote availability check at connection startup to eliminate unresponsive clients.
Allowed values: Default value: true. |
run_logon_script |
Runs the logon script provided by the domain controller after the VPN tunnel is established.
Allowed values: Default value: false. |
Templates
You can use the following provisioning file templates to create provisioning files specific to your organization. You can change the settings.
Copy and paste the scripts in a text editor, such as Notepad, edit the settings to meet your requirements, and save the file with a .pro extension.
Requirement
You must specify the gateway address. The other fields are optional.
Note
If you change the VPN portal port in the firewall, you must change it in the provisioning file.
Single connection
Multiple connections
Multiple gateways
Provisioning file: 2FA settings
| Setting | Description |
|---|---|
otp |
Specifies if a one-time password (OTP) is required for authentication when connecting. This shows a third input box to enter the OTP code in the Sophos Connect client.
Allowed values: Default value: false. |
2fa |
Specifies the method of two-factor authentication (2FA) to use.
Allowed values: Default value: 1. The allowed values are as follows:
|
If you've configured more than one Duo method, users must enter the following in the third input box:
- Duo Push:
push - Duo phone:
phone - Duo SMS:
sms(The sign-in screen appears again. Users must enter the username, password, and verification code.) - Duo token: The passcode.
Note
If users need to enter an OTP token or code, the Sophos Connect client shows the sign-in screen twice when they sign for the first time. The first sign-in downloads the configuration file and the second establishes the connection.
Templates
Sophos Firewall 2FA with OTP
Duo 2FA
You can automatically download and import the remote access VPN provisioning file (.pro) to the Sophos Connect clients on users' endpoints using a script through Active Directory Group Policy Object (GPO).
Import provisioning file to Sophos Connect client
To download and import the provisioning file, do as follows:
- Open a blank file in a text editor, such as Notepad, and paste the following script:
@echo off REM Use the automatic import feature of the Sophos Connect client to download and import the .pro file REM Wait for scvpn service to be available :WAIT2 timeout /t 5 > NUL for /f "tokens=4" %%s in ('sc query scvpn ^| find "STATE"') do if NOT "%%s"=="RUNNING" goto WAIT2 echo Service is now running! REM scvpn service is available. Download the .pro file from a centrally-hosted location. Make sure you enter your URL and the filename you want. powershell -Command "Invoke-WebRequest <full_web_url_where_pro_file_is_hosted> -OutFile download_import_scc.pro" REM Copy the downloaded .pro file to the SCC import folder for the automatic import feature to act copy download_import_scc.pro "C:\Program Files (x86)\Sophos\Connect\import\"Note
The script waits for the scvpn service to run after the endpoint starts. So, don't stop the Sophos Connect service in your startup apps.
- Save the file with a
.batextension. - To add the path where you've saved the script, do as follows:
- On the Windows Server, open Group Policy Management Console (GPMC) and click Group Policy Management.
- Click the group policy that applies to users' endpoints, click Computer Configuration, and click Policies.
- Under Windows Settings, click Scripts, and double-click Startup.
- Follow the instructions to add the
.batfile. See Working with startup scripts using the Local Group Policy Editor.
- To apply the script, run the following command:
gpupdate /forceWhen users start their endpoints, the
scvpnservice starts, and the script downloads the.profile from the server to the Sophos Connect import folder.The Sophos Connect client automatically imports the
.profile from this folder and deletes the file from the folder. It then connects to the VPN portal through the gateway configured in the.profile and pulls the remote access IPsec VPN and remote access SSL VPN configurations.