NAT with route-based IPsec when local and remote subnets are the same
Zitat von mpachmann am 10. Oktober 2025, 10:03 Uhrhttps://docs.sophos.com/nsg/sophos-firewall/21.5/Help/en-us/webhelp/onlinehelp/AdministratorHelp/SiteToSiteVPN/HowToArticles/S2sVPNIPsecConnectionRBVPNNATSameSubnets/index.html
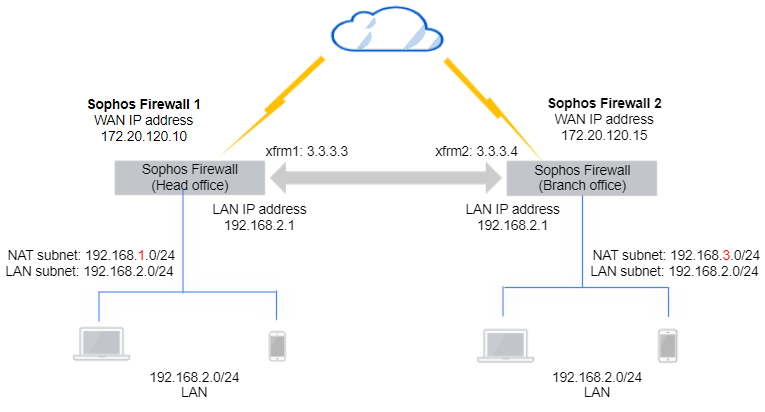
You can configure Network Address Translation (NAT) for route-based IPsec VPN tunnels when the subnets are the same in the local and remote firewalls.
The configuration differs for the two types of route-based VPN tunnels as follows:
- For any-to-any subnets: You must configure SNAT and DNAT rules.
- With traffic selectors: You must configure the NAT settings on Site-to-site VPN > IPsec connections. See NAT with policy-based IPsec when local and remote subnets are the same.
This article shows an example configuration for tunnel interfaces with any-to-any subnets.
- Configure the following:
- IPsec connection
- Inbound and outbound firewall rules
- SD-WAN route
- Do as follows in the head office and branch office firewalls:
- Configure a DNAT rule with a reflexive (SNAT) rule.
- Review the SNAT rule.
Head office firewall
Configure DNAT and SNAT rules in the head office firewall (Sophos Firewall 1).
Configure a DNAT rule
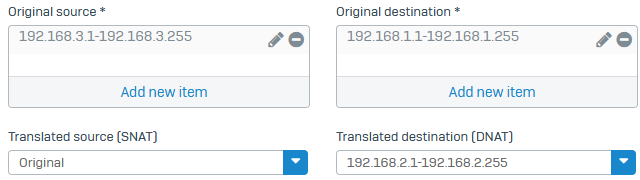
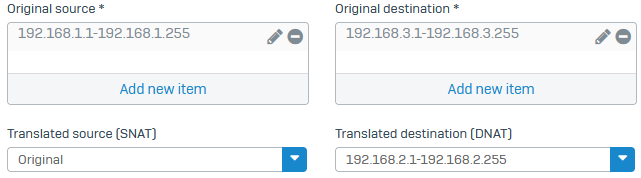
Add a DNAT rule to translate incoming traffic that arrives at the NAT IP range to the local subnet's IP range.
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the branch office NAT range object (example:
192.168.3.1 to 192.168.3.255).- Set Translated source to Original.
- Set Original destination to the IP range object you created for the translation (example:
192.168.1.1 to 192.168.1.255).- Set Translated destination to the actual local subnet object (example:
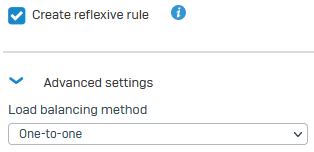
192.168.2.1 to 192.168.2.255).- Select Create reflexive rule to create a corresponding SNAT rule for outgoing traffic.
- For Load balancing method, select One-to-one.
- Click Save.
Review the SNAT rule
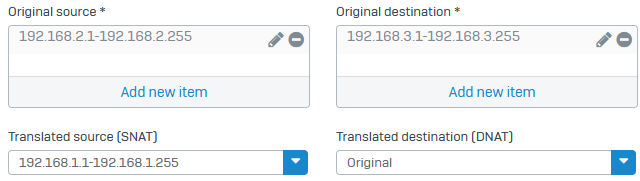
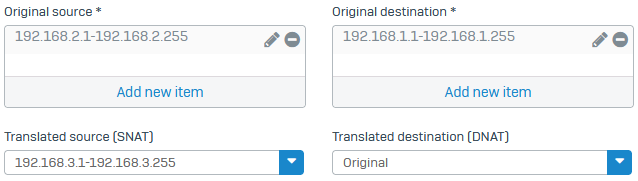
Check the SNAT rule for outgoing traffic to translate the local subnet's IP range to the object you created for translation.
- Go to Rules and policies > NAT rules.
- Click the reflexive rule you've created.
Example:
Reflexive_NAT#_<DNAT rulename>- Review the source translation settings. The example settings are as follows:
- Original source:
192.168.2.1 to 192.168.2.255- Translated source:
192.168.1.1 to 192.168.1.255- Original destination:
192.168.3.1 to 192.168.3.255- Translated destination: Original
Outgoing traffic is translated from the subnet's actual IP range to the translated IP range.
Branch office firewall
Configure DNAT and SNAT rules in the branch office firewall (Sophos Firewall 2).
Configure a DNAT rule
Add a DNAT rule to translate incoming traffic that arrives at the NAT IP range to the local subnet's IP range.
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the head office NAT range object (example:
192.168.1.1 to 192.168.1.255).- Set Translated source to Original.
- Set Original destination to the IP range object you created for the translation (example:
192.168.3.1 to 192.168.3.255).- Set Translated destination to the actual local subnet object (example:
192.168.2.1 to 192.168.2.255).- Select Create reflexive rule to create a corresponding SNAT rule for outgoing traffic.
- For Load balancing method, select One-to-one.
- Click Save.
Review the SNAT rule
Check the SNAT rule for outgoing traffic to translate the local subnet's IP range to the object you created for translation.
- Go to Rules and policies > NAT rules.
- Click the reflexive rule you've created.
Example:
Reflexive_NAT#_<DNAT rulename>- Review the source translation settings. The example settings are as follows:
- Original source:
192.168.2.1 to 192.168.2.255- Translated source:
192.168.3.1 to 192.168.3.255- Original destination:
192.168.1.1 to 192.168.1.255- Translated destination: Original
Outgoing traffic is translated from the subnet's actual IP range to the translated IP range.
You can configure Network Address Translation (NAT) for route-based IPsec VPN tunnels when the subnets are the same in the local and remote firewalls.
The configuration differs for the two types of route-based VPN tunnels as follows:
- For any-to-any subnets: You must configure SNAT and DNAT rules.
- With traffic selectors: You must configure the NAT settings on Site-to-site VPN > IPsec connections. See NAT with policy-based IPsec when local and remote subnets are the same.
This article shows an example configuration for tunnel interfaces with any-to-any subnets.
- Configure the following:
- IPsec connection
- Inbound and outbound firewall rules
- SD-WAN route
- Do as follows in the head office and branch office firewalls:
- Configure a DNAT rule with a reflexive (SNAT) rule.
- Review the SNAT rule.
Head office firewall
Configure DNAT and SNAT rules in the head office firewall (Sophos Firewall 1).
Configure a DNAT rule
Add a DNAT rule to translate incoming traffic that arrives at the NAT IP range to the local subnet's IP range.
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the branch office NAT range object (example:
192.168.3.1 to 192.168.3.255). - Set Translated source to Original.
- Set Original destination to the IP range object you created for the translation (example:
192.168.1.1 to 192.168.1.255). - Set Translated destination to the actual local subnet object (example:
192.168.2.1 to 192.168.2.255). - Select Create reflexive rule to create a corresponding SNAT rule for outgoing traffic.
- For Load balancing method, select One-to-one.
- Click Save.
Review the SNAT rule
Check the SNAT rule for outgoing traffic to translate the local subnet's IP range to the object you created for translation.
- Go to Rules and policies > NAT rules.
- Click the reflexive rule you've created.
Example:
Reflexive_NAT#_<DNAT rulename> - Review the source translation settings. The example settings are as follows:
- Original source:
192.168.2.1 to 192.168.2.255 - Translated source:
192.168.1.1 to 192.168.1.255 - Original destination:
192.168.3.1 to 192.168.3.255 - Translated destination: Original
Outgoing traffic is translated from the subnet's actual IP range to the translated IP range.
- Original source:
Branch office firewall
Configure DNAT and SNAT rules in the branch office firewall (Sophos Firewall 2).
Configure a DNAT rule
Add a DNAT rule to translate incoming traffic that arrives at the NAT IP range to the local subnet's IP range.
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the head office NAT range object (example:
192.168.1.1 to 192.168.1.255). - Set Translated source to Original.
- Set Original destination to the IP range object you created for the translation (example:
192.168.3.1 to 192.168.3.255). - Set Translated destination to the actual local subnet object (example:
192.168.2.1 to 192.168.2.255). - Select Create reflexive rule to create a corresponding SNAT rule for outgoing traffic.
- For Load balancing method, select One-to-one.
- Click Save.
Review the SNAT rule
Check the SNAT rule for outgoing traffic to translate the local subnet's IP range to the object you created for translation.
- Go to Rules and policies > NAT rules.
- Click the reflexive rule you've created.
Example:
Reflexive_NAT#_<DNAT rulename> - Review the source translation settings. The example settings are as follows:
- Original source:
192.168.2.1 to 192.168.2.255 - Translated source:
192.168.3.1 to 192.168.3.255 - Original destination:
192.168.1.1 to 192.168.1.255 - Translated destination: Original
Outgoing traffic is translated from the subnet's actual IP range to the translated IP range.
- Original source: