Applocker GPO
Zitat von mpachmann am 28. Februar 2024, 16:17 Uhrhttps://administrator.de/tutorial/windows-10-apps-mit-applocker-sperren-277893.html
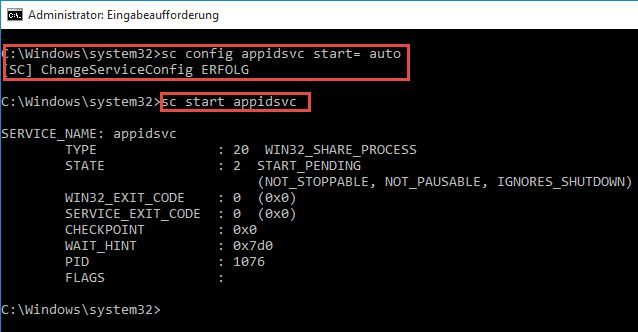
Schritt 1: Dienst Anwendungsidentität (AppIDSvc) auf automatisch stellen und starten
Damit unsere in den nächsten Schritten erstellten Richtlinien Anwendung finden müssen wir den Dienst Anwendungsidentität (AppIDSvc) starten und den Startmodus auf Automatisch stellen. Da unter Windows 10 in der Computerverwaltung die Umstellung der Startart des Dienstes verweigert wird, müssen wir uns auf die Konsole begeben.
Dazu starten wir eine CMD-Shell mit Admin-Rechten:In diese geben wir nun den folgende zwei Befehle nacheinander ein:
(Bitte auf das Leerzeichen nach dem Gleichheitszeichen achten, dies muss dort stehen)1
2sc config appidsvc start= auto sc start appidsvchttps://pureinfotech.com/list-environment-variables-windows-10/Windows 11 (and 10) default environment variables
VARIABLE WINDOWS 10 AND WINDOWS 11 %ALLUSERSPROFILE% C:\ProgramData %APPDATA% C:\Users\{username}\AppData\Roaming %COMMONPROGRAMFILES% C:\Program Files\Common Files %COMMONPROGRAMFILES(x86)% C:\Program Files (x86)\Common Files %CommonProgramW6432% C:\Program Files\Common Files %COMSPEC% C:\Windows\System32\cmd.exe %HOMEDRIVE% C:\ %HOMEPATH% C:\Users\{username} %LOCALAPPDATA% C:\Users\{username}\AppData\Local %LOGONSERVER% \\{domain_logon_server} %PATH% C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem %PathExt% .com;.exe;.bat;.cmd;.vbs;.vbe;.js;.jse;.wsf;.wsh;.msc %PROGRAMDATA% C:\ProgramData %PROGRAMFILES% C:\Program Files %ProgramW6432% C:\Program Files %PROGRAMFILES(X86)% C:\Program Files (x86) %PROMPT% $P$G %SystemDrive% C: %SystemRoot% C:\Windows %TEMP% C:\Users\{username}\AppData\Local\Temp %TMP% C:\Users\{username}\AppData\Local\Temp %USERDOMAIN% Userdomain associated with current user. %USERDOMAIN_ROAMINGPROFILE% Userdomain associated with roaming profile. %USERNAME% {username} %USERPROFILE% C:\Users\{username} %WINDIR% C:\Windows %PUBLIC% C:\Users\Public %PSModulePath% %SystemRoot%\system32\WindowsPowerShell\v1.0\Modules\ %OneDrive% C:\Users\{username}\OneDrive %DriverData% C:\Windows\System32\Drivers\DriverData %CD% Outputs current directory path. (Command Prompt.) %CMDCMDLINE% Outputs command line used to launch current Command Prompt session. (Command Prompt.) %CMDEXTVERSION% Outputs the number of current command processor extensions. (Command Prompt.) %COMPUTERNAME% Outputs the system name. %DATE% Outputs current date. (Command Prompt.) %TIME% Outputs time. (Command Prompt.) %ERRORLEVEL% Outputs the number of defining exit status of previous command. (Command Prompt.) %PROCESSOR_IDENTIFIER% Outputs processor identifier. %PROCESSOR_LEVEL% Outputs processor level. %PROCESSOR_REVISION% Outputs processor revision. %NUMBER_OF_PROCESSORS% Outputs the number of physical and virtual cores. %RANDOM% Outputs random number from 0 through 32767. %OS% Windows_NT https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/applocker/understanding-the-path-rule-condition-in-applocker
The path condition identifies an application by its location in the file system of the computer or on the network.
Path rules that use the deny action, are less effective than other types of rules, because a user (or malware acting as a user) can easily copy the file to a different location to run it. Because path rules specify locations within the file system, you should ensure that there are no subdirectories that are writable by nonadministrators. For example, if you create a path rule using the allow action for C:\, any file under that location can run, including file within users' profiles. The following table describes the advantages and disadvantages of the path condition.
Path condition advantages Path condition disadvantages
- You can easily control many folders or a single file.
- You can use the asterisk (*) as a wildcard character within path rules.
- It might be less secure if a rule that is configured to use a folder path contains subfolders that are writable by nonadministrators.
- You must specify the full path to a file or folder when creating path rules so that the rule is properly enforced.
AppLocker doesn't enforce rules that specify paths with short names. You should always specify the full path to a file or folder when creating path rules so that the rule is properly enforced.
The asterisk (*) wildcard character can be used within Path field. The asterisk (*) character used by itself represents any path. When combined with any string value, the rule is limited to the path of the file and all the files under that path. For example, %ProgramFiles%\Internet Explorer\* indicates that the rule affects all files and subfolders within the Internet Explorer folder.
AppLocker uses path variables for well-known directories in Windows. Path variables aren't environment variables. The AppLocker engine can only interpret AppLocker path variables. The following table details these path variables.
Windows directory or drive AppLocker path variable Windows environment variable Windows %WINDIR% %SystemRoot% System32 and sysWOW64 %SYSTEM32% %SystemDirectory% Windows installation directory %OSDRIVE% %SystemDrive% Program Files %PROGRAMFILES% %ProgramFiles% and %ProgramFiles(x86)% Removable media (for example, CD or DVD) %REMOVABLE% Removable storage device (for example, USB flash drive) %HOT%
https://administrator.de/tutorial/windows-10-apps-mit-applocker-sperren-277893.html
Schritt 1: Dienst Anwendungsidentität (AppIDSvc) auf automatisch stellen und starten
Damit unsere in den nächsten Schritten erstellten Richtlinien Anwendung finden müssen wir den Dienst Anwendungsidentität (AppIDSvc) starten und den Startmodus auf Automatisch stellen. Da unter Windows 10 in der Computerverwaltung die Umstellung der Startart des Dienstes verweigert wird, müssen wir uns auf die Konsole begeben.
Dazu starten wir eine CMD-Shell mit Admin-Rechten:
In diese geben wir nun den folgende zwei Befehle nacheinander ein:
(Bitte auf das Leerzeichen nach dem Gleichheitszeichen achten, dies muss dort stehen)
2
sc config appidsvc start= auto
sc start appidsvcWindows 11 (and 10) default environment variables
| VARIABLE | WINDOWS 10 AND WINDOWS 11 |
|---|---|
| %ALLUSERSPROFILE% | C:\ProgramData |
| %APPDATA% | C:\Users\{username}\AppData\Roaming |
| %COMMONPROGRAMFILES% | C:\Program Files\Common Files |
| %COMMONPROGRAMFILES(x86)% | C:\Program Files (x86)\Common Files |
| %CommonProgramW6432% | C:\Program Files\Common Files |
| %COMSPEC% | C:\Windows\System32\cmd.exe |
| %HOMEDRIVE% | C:\ |
| %HOMEPATH% | C:\Users\{username} |
| %LOCALAPPDATA% | C:\Users\{username}\AppData\Local |
| %LOGONSERVER% | \\{domain_logon_server} |
| %PATH% | C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem |
| %PathExt% | .com;.exe;.bat;.cmd;.vbs;.vbe;.js;.jse;.wsf;.wsh;.msc |
| %PROGRAMDATA% | C:\ProgramData |
| %PROGRAMFILES% | C:\Program Files |
| %ProgramW6432% | C:\Program Files |
| %PROGRAMFILES(X86)% | C:\Program Files (x86) |
| %PROMPT% | $P$G |
| %SystemDrive% | C: |
| %SystemRoot% | C:\Windows |
| %TEMP% | C:\Users\{username}\AppData\Local\Temp |
| %TMP% | C:\Users\{username}\AppData\Local\Temp |
| %USERDOMAIN% | Userdomain associated with current user. |
| %USERDOMAIN_ROAMINGPROFILE% | Userdomain associated with roaming profile. |
| %USERNAME% | {username} |
| %USERPROFILE% | C:\Users\{username} |
| %WINDIR% | C:\Windows |
| %PUBLIC% | C:\Users\Public |
| %PSModulePath% | %SystemRoot%\system32\WindowsPowerShell\v1.0\Modules\ |
| %OneDrive% | C:\Users\{username}\OneDrive |
| %DriverData% | C:\Windows\System32\Drivers\DriverData |
| %CD% | Outputs current directory path. (Command Prompt.) |
| %CMDCMDLINE% | Outputs command line used to launch current Command Prompt session. (Command Prompt.) |
| %CMDEXTVERSION% | Outputs the number of current command processor extensions. (Command Prompt.) |
| %COMPUTERNAME% | Outputs the system name. |
| %DATE% | Outputs current date. (Command Prompt.) |
| %TIME% | Outputs time. (Command Prompt.) |
| %ERRORLEVEL% | Outputs the number of defining exit status of previous command. (Command Prompt.) |
| %PROCESSOR_IDENTIFIER% | Outputs processor identifier. |
| %PROCESSOR_LEVEL% | Outputs processor level. |
| %PROCESSOR_REVISION% | Outputs processor revision. |
| %NUMBER_OF_PROCESSORS% | Outputs the number of physical and virtual cores. |
| %RANDOM% | Outputs random number from 0 through 32767. |
| %OS% | Windows_NT |
The path condition identifies an application by its location in the file system of the computer or on the network.
Path rules that use the deny action, are less effective than other types of rules, because a user (or malware acting as a user) can easily copy the file to a different location to run it. Because path rules specify locations within the file system, you should ensure that there are no subdirectories that are writable by nonadministrators. For example, if you create a path rule using the allow action for C:\, any file under that location can run, including file within users' profiles. The following table describes the advantages and disadvantages of the path condition.
| Path condition advantages | Path condition disadvantages |
|---|---|
|
|
AppLocker doesn't enforce rules that specify paths with short names. You should always specify the full path to a file or folder when creating path rules so that the rule is properly enforced.
The asterisk (*) wildcard character can be used within Path field. The asterisk (*) character used by itself represents any path. When combined with any string value, the rule is limited to the path of the file and all the files under that path. For example, %ProgramFiles%\Internet Explorer\* indicates that the rule affects all files and subfolders within the Internet Explorer folder.
AppLocker uses path variables for well-known directories in Windows. Path variables aren't environment variables. The AppLocker engine can only interpret AppLocker path variables. The following table details these path variables.
| Windows directory or drive | AppLocker path variable | Windows environment variable |
|---|---|---|
| Windows | %WINDIR% | %SystemRoot% |
| System32 and sysWOW64 | %SYSTEM32% | %SystemDirectory% |
| Windows installation directory | %OSDRIVE% | %SystemDrive% |
| Program Files | %PROGRAMFILES% | %ProgramFiles% and %ProgramFiles(x86)% |
| Removable media (for example, CD or DVD) | %REMOVABLE% | |
| Removable storage device (for example, USB flash drive) | %HOT% |